Symmetric key Cryptography
Symmetric key cryptography is a class of algorithms where Alice and Bob share a secret key.These algorithms are primarily used to achieve confidentiality.
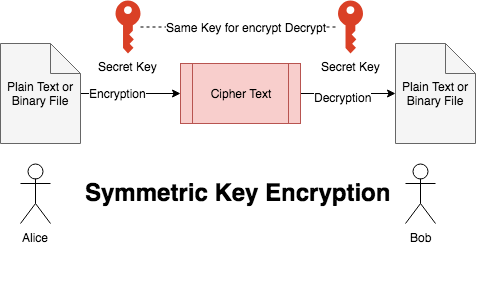
Symmetric algorithms are ideally suited for confidentiality. To use a symmetric algorithm , Alice transforms a plaintext message to ciphertext using a symmetric algorithm (AES/Des/3DES..) and a key.
Alice transmits the ciphertext to Bob. Bob uses the same key to transform the ciphertext back into the plaintext
Feature of Symmetric key
| Symmetric algorithms | Integrity | Confidentiality | Identification & Authentication | Non Repudiation | Key Distribution |
|---|---|---|---|---|---|
| Encryption | No | Yes | No | No | No |
| Message Authentication Code | Yes | No | Yes | No | No |
| key Transport | No | No | No | No | Yes with TTP (Trusted Third Party) |
In this chapter we will be discussing below topics related to Symmetric key Cryptography.
- Modes of Operation
- Authenticated Encrypted Modes
- Initial Vector requirement
- Some Examples Block Cipher Algorithms
- Data Encryption Standard
- Triple Data Encryption Standard (TDEA)
- SkipJack
- Advanced Encryption Standard
- RC4
- BlowFish
- Hash based Symmetric key Algorithms
Block ciphers Modes of Operation
Block ciphers modes provides encryption but not message integrity
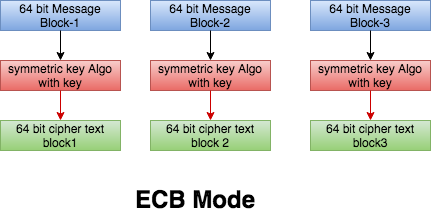
ECB:
The Electronic Codebook (ECB), The message is divided into blocks, and each block is encrypted separately, this is the simplest encryption and decryption mode.
Example Ciphers
AES-128-ECB,AES-192-ECB,AES-256-ECB,BF-ECB,CAMELLIA-128-ECB,CAMELLIA-192-ECB,CAMELLIA-256-ECB,CAST5-ECB,DES-ECB,IDEA-ECB,RC2-ECB,RC5-ECB,SEED-ECB,AES-128-ECB,AES-192-ECB,AES-256-ECB,BF-ECB,CAMELLIA-128-ECB,CAMELLIA-192-ECB,CAMELLIA-256-ECB,CAST5-ECB,DES-ECB,IDEA-ECB,RC2-ECB,RC5-ECB,SEED-ECB
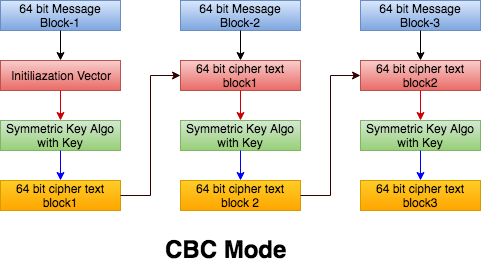
CBC
Cipher Block Chaining (CBC) mode an IV-based encryption scheme , each block of plaintext is XORed with the previous ciphertext block before being encrypted. This way, each ciphertext block depends on all plaintext blocks processed up to that point. To make each message unique, an initialization vector must be used in the first block
Example Ciphers
AES-128-CBC,AES-128-CBC-HMAC-SHA1,AES-128-CBC-HMAC-SHA256,AES-192-CBC,AES-256-CBC,AES-256-CBC-HMAC-SHA1,AES-256-CBC-HMAC-SHA256,AES128 => AES-128-CBC,AES192 => AES-192-CBC,AES256 => AES-256-CBC,BF => BF-CBC,BF-CBC,CAMELLIA-128-CBC,CAMELLIA-192-CBC,CAMELLIA-256-CBC,CAMELLIA128 => CAMELLIA-128-CBC,CAMELLIA192 => CAMELLIA-192-CBC,CAMELLIA256 => CAMELLIA-256-CBC,CAST => CAST5-CBC,CAST-cbc => CAST5-CBC,CAST5-CBC,DES => DES-CBC,DES-CBC,DES-EDE-CBC,DES-EDE3-CBC,DES3 => DES-EDE3-CBC,DESX => DESX-CBC,DESX-CBC,IDEA => IDEA-CBC,IDEA-CBC,RC2 => RC2-CBC,RC2-40-CBC,RC2-64-CBC,RC2-CBC,RC5 => RC5-CBC,RC5-CBC,SEED => SEED-CBC,SEED-CBC,AES-128-CBC,AES-128-CBC-HMAC-SHA1,AES-128-CBC-HMAC-SHA256,AES-192-CBC
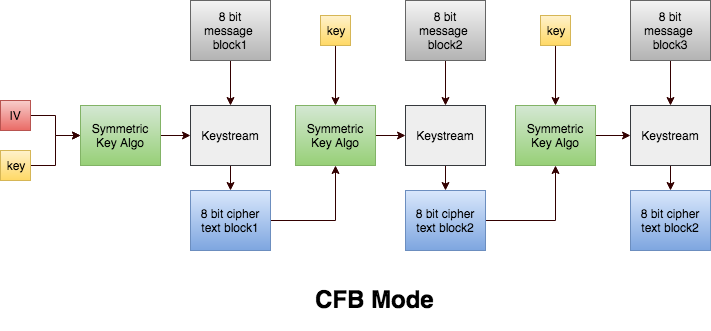
CFB
Cipher Feedback (CFB) mode is a confidentiality mode that features the feedback of successive ciphertext segments into the input blocks of the forward cipher to generate output blocks that are exclusive-ORed with the plaintext to produce the ciphertext, and vice versa. The CFB mode requires an IV as the initial input block
Example Ciphers
AES-128-CFB,AES-128-CFB1,AES-128-CFB8,AES-192-CFB,AES-192-CFB1,AES-192-CFB8,AES-256-CFB,AES-256-CFB1,AES-256-CFB8,BF-CFB,CAMELLIA-128-CFB,CAMELLIA-128-CFB1,CAMELLIA-128-CFB8,CAMELLIA-192-CFB,CAMELLIA-192-CFB1,CAMELLIA-192-CFB8,CAMELLIA-256-CFB,CAMELLIA-256-CFB1,CAMELLIA-256-CFB8,CAST5-CFB,DES-CFB,DES-CFB1,DES-CFB8,DES-EDE-CFB,DES-EDE3-CFB,DES-EDE3-CFB1,DES-EDE3-CFB8,IDEA-CFB,RC2-CFB,RC5-CFB,SEED-CFB
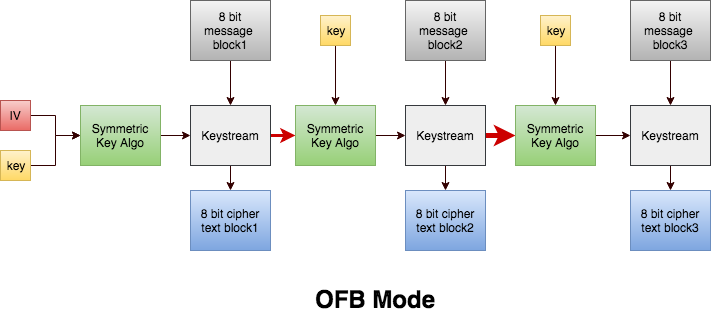
OFB
The Output Feedback (OFB) mode makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext
Example Ciphers
AES-128-OFB,AES-192-OFB,AES-256-OFB,BF-OFB,CAMELLIA-128-OFB,CAMELLIA-192-OFB,CAMELLIA-256-OFB,CAST5-OFB,DES-EDE-OFB,DES-EDE3-OFB,DES-OFB,IDEA-OFB,RC2-OFB,RC5-OFB,SEED-OFB,AES-128-OFB,AES-192-OFB,AES-256-OFB,BF-OFB,CAMELLIA-128-OFB,CAMELLIA-192-OFB,CAMELLIA-256-OFB,CAST5-OFB,DES-EDE-OFB,DES-EDE3-OFB,DES-OFB,IDEA-OFB,RC2-OFB,RC5-OFB,SEED-OFB
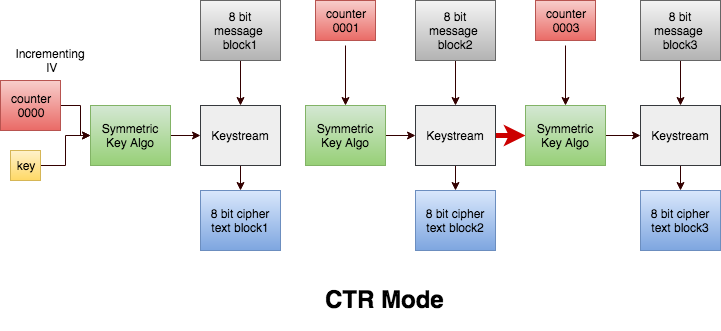
CTR
The CTR mode has similar characteristics to OFB, but also allows a random access property during decryption. CTR mode is well suited to operate on a multi-processor machine where blocks can be encrypted in parallel. Furthermore, it does not suffer from the short-cycle problem that can affect OFB.
Example Ciphers
AES-128-CTR,AES-192-CTR,AES-256-CTR,AES-128-CTR,AES-192-CTR,AES-256-CTR
XTS
An IV-based encryption scheme, the mode works by applying a tweakable blockcipher (secure as a strong-PRP) to each n-bit chunk. For messages with lengths not divisible by n, the last two blocks are treated specially. The only allowed use of the mode is for encrypting data on a block-structured storage device. The narrow width of the underlying PRP and the poor treatment of fractional final blocks are problems. More efficient but less desirable than a (wide-block) PRP-secure blockcipher would be.
Example Ciphers
Authenticated encryption Modes
Authenticated encryption provides both encryption and message integrity
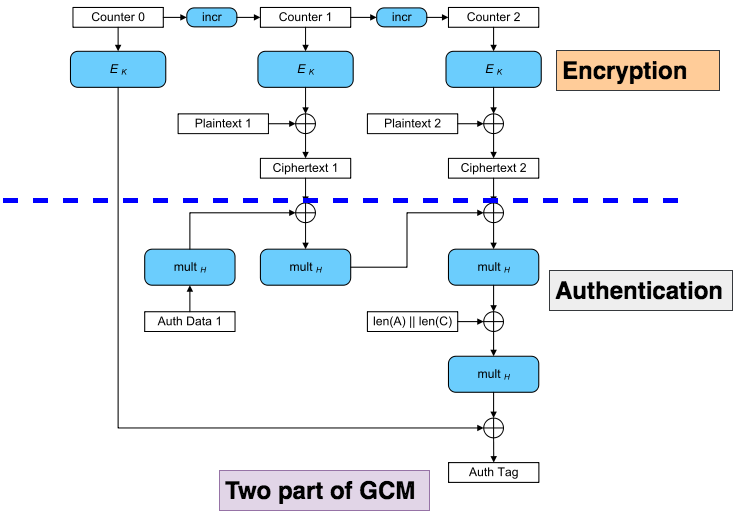
GCM
Galois/Counter Mode (GCM) A nonce-based AEAD scheme that combines CTR mode encryption and a GF(2128)-based universal hash function. Good efficiency characteristics for some implementation environments. Good provably-secure results assuming minimal tag truncation. Attacks and poor provable-security bounds in the presence of substantial tag truncation. Can be used as a nonce-based MAC, which is then called GMAC. Questionable choice to allow nonces other than 96-bits. Recommend restricting nonces to 96-bits and tags to at least 96 bits. Widely standardized and used.
Example Ciphers
CCM
CCM mode (Counter with CBC-MAC), A nonce-based AEAD scheme that combines CTR mode encryption and the raw CBC-MAC. Inherently serial, limiting speed in some contexts. Provably secure, with good bounds, assuming the underlying blockcipher is a good PRP. Ungainly construction that demonstrably does the job. Simpler to implement than GCM. Can be used as a nonce-based MAC. Widely standardized and used.
Example Ciphers
Initialization Vectors
Generation of Initial Vectors - The CBC, CFB, and OFB modes require an initialization vector as input, in addition to the plaintext. An IV must be generated for each execution of the encryption operation, and the same IV is necessary for the corresponding execution of the decryption operation - For the CBC and CFB modes, the IVs must be unpredictable